Remote work security is quickly becoming a hot topic.
Today, 44% of workers in the UK are remote employees. Only 3 out of 10 companies still insist on staff being on-site full-time.
With so many people working remotely, it’s no wonder that companies are focussing on remote work security risks.
I’m not making this up. Recently, we saw that improved cybersecurity will impact the future of remote work.
Join me as I explore 9 remote work security risks. Even better, I’ll provide a solution for each common security risk.
Ready? Let’s roll.
Are You Aware Of These 9 Remote Work Security Risks?
In a hurry? Here are 9 remote work security risks every company faces. I’ve also included ways to mitigate these cybersecurity risks.
Cybersecurity Risks | Solutions |
|---|---|
Limited or no oversight of how remote workers handle data. | Use data loss prevention (DLP) tools and enforce strict access controls. Conduct regular security training and audits. |
Challenges in complying with data regulations. | Adopt a data residency solution that ensures data compliance across borders. Regularly update data policies and training. |
Increased susceptibility to phishing and other social engineering attacks. | Enhance training on identifying phishing attempts and secure communication protocols. Use two-factor authentication. |
Increased vulnerability to AI-driven attacks. | Implement advanced threat detection systems that can identify and respond to AI-driven attacks. Encourage regular team interactions. |
Unsecured and vulnerable hardware. | Require secure configurations and regular updates. Implement a policy for the use of personal devices (BYOD). |
Unsecured and vulnerable networks. | Encourage the use of VPNs and secure, private Wi-Fi networks. Implement network security policies for remote environments. |
Networks shared with others. | Advise remote workers to secure their home networks and devices. Use network segmentation and monitor network traffic. |
Webcam hacking and Zoombombing. | Use secure, enterprise-grade conferencing tools with updated security settings. Educate users on digital meeting etiquette. |
Vulnerabilities in chat platforms. | Use encrypted chat platforms and provide training on recognising signs of infiltration. Monitor platform security regularly. |
Got a bit more time with me? Excellent! Let me walk you through these 9 remote work security risks. Let’s start with the biggest concern.
1. Limited Oversight
Limited oversight of how remote workers handle data is a significant security concern.
CISCO found that 73% of companies believe a cyberattack will happen in the next 12 to 24 months.
But there’s even more bad news.
52% of companies that experienced cyberattacks in the last 8 months had financial losses exceeding $300,000. That’s a lot of money.
The mayor culprit?
Employees are accessing and saving data via unsecured networks and devices.
The same report found that most employees use their personal devices for remote work. Many employees (me included!) have mobile app versions of remote work tools, like Slack on my phone.
These blurred lines make it difficult to keep data in a secure environment.
The solution? Data Loss Prevention (DLP) tools.
Let me explain.
DLP tools, like Trellix, are specialised software systems. They’re designed to detect and prevent the unauthorised use and transmission of confidential information.
If sensitive data is detected in unauthorised locations or misused, DLP tools can execute predefined actions such as blocking data transfers, alerting administrators, or quarantining data.
So, you can create a safe zone, for instance, in an employee's home office, and allow them to access sensitive company data only when in the safe zone.
But this isn’t the only remote work security risk related to data control.

Discover how to slash your salary costs by 80%
Get our exact process for hiring amazing overseas talent from South Africa. Includes copy-and-paste templates and a detailed salary guide.
2. Not Complying With Data Regulations
Some countries, like Russia and China, have specific laws requiring the storage of data about their citizens within their borders.
But there’s more.
Australia requires all health records to be stored locally. Canada and Indonesia require some personal data to be stored and accessed only within the country.
An employee working with this data residing in a different country may violate these laws.
Another risk is that cross-border data transfers can be hacked or intercepted.
So, how do you ensure your company can adhere to global data regulations when hiring remote employees? Especially if your company regularly handles sensitive and personal data?
Use local data centers. Local cloud services can offer regional data storage and access.
And here’s my pro tip: Develop a robust data localisation policy. This policy should have clear guidelines on where data should be stored and processed. Ensure your employees are familiar with it.
Now that we’ve found solutions for limited employee oversight and complying with data regulations, what’s next?
My pet peeve: phishing attacks.
3. Phishing And Social Engineering Attacks

Info Security found a 600% increase in reported phishing attacks.
Info Security found a 600% increase in reported phishing attacks. Globally, phishing attacks are costing businesses around $3.2 billion yearly.
What is a phishing attack?
A phishing attack is when someone tries to trick you into giving them your private information by pretending to be a trustworthy person or company in an email or other communication.
For example, you might get an email that looks like it's from your bank asking you to click a link and enter your account password. The email might look real, but it's actually from a scammer trying to steal your password.
I’ve had my fair share of phishing attacks as a remote worker. Most of the time, I get an email from a coworker or manager asking me for a quick favour.
Luckily, it’s easy to spot these attacks. Generally, the grammar is horrible. The sender’s email address is also always something terrible, like many numbers and random characters.
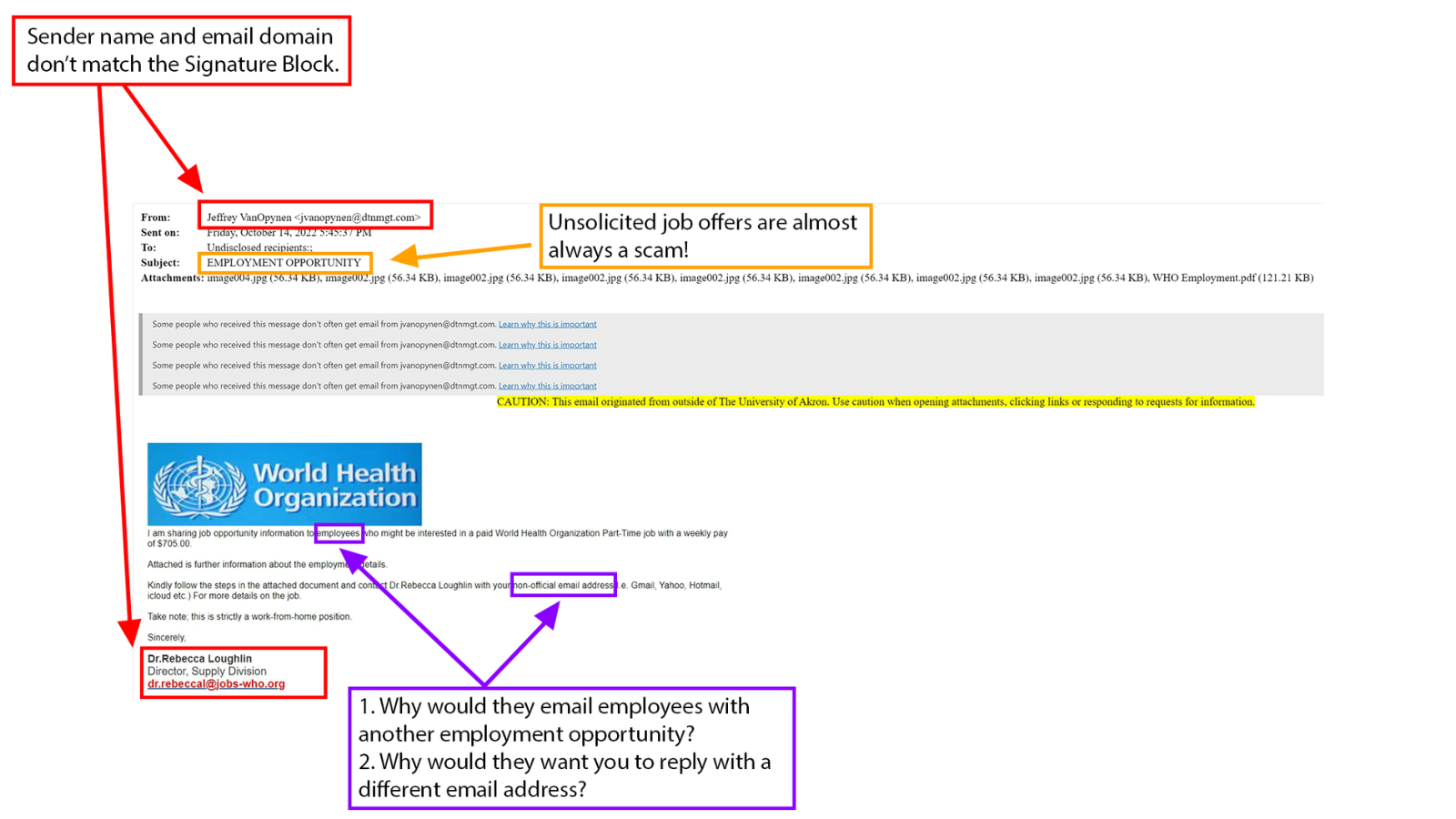
Example of a phising email.
My tip for preventing phishing attacks?
First, make your employees aware of them. Next, check to see if the email address and links look legitimate. And when in doubt, contact the sender directly using a phone number or email you know is safe.
Now, let’s enter the scary world of AI-driven attacks.
Yes, there are even more remote work security risks to deal with.
Hire remote talent from South Africa & slash salary costs by 80%
Salaries start from £8,000 per year!
4. AI-Driven attacks
I never thought I’d write this, but here I am: AI poses a cybersecurity threat for remote work. Let’s first look at what an AI-driven attack is.
AI-driven attacks are when someone uses artificial intelligence to create smarter ways to break into computer systems or trick people. These attacks could be via malware or even phishing.
These attacks can be harder to spot because they learn and adapt to make themselves seem more believable.
Remember that bad grammar was a sure sign of a phishing attack?
Scammers are now using AI to help them craft ever more believable (and grammatically correct) emails!
To protect against these attacks, companies use advanced threat detection systems.
Also, encouraging people to talk regularly with their team members can help everyone stay aware of any strange things happening, like receiving odd emails, and report them quickly.
So, teach your remote employees to regularly stay in touch via messaging apps and report suspicious activity as soon as they become aware of it.
5. Unsecured Hardware
Remember I was discussing limited oversight being a mayor remote work security concern? Well, limited oversight is an overarching problem with two legs.
Let’s examine the first leg: unsecured hardware.
A CISCO report found that 85% of companies said their remote workers access company platforms via unmanaged devices. In fact, 43% of employees spend 20% of their time logging on to company networks from these unmanaged devices.
The stats get even scarier.
29% of companies report that employees hop between at least 6 networks every week. But why is this such a considerable risk?
These unmanaged devices may be susceptible to cyberattacks, whether viruses, malware, or even ransomware.
Because the company doesn’t control what employees do with these devices, there’s no protection.
How do you mitigate this remote work security risk?
Empower your employees to update their devices regularly. Require the latest secure configurations. And finally, implement a policy for using personal devices (BYOD).
Now, let’s move on to the second leg.
6. Vulnerable Networks

Home-office networks are 3.5 times more likely than corporate networks to be infected with at least one type of malware.
Like unmanaged devices, unmanaged networks also pose a significant security risk.
A BitSight study found that home-office networks are 3.5 times more likely than corporate networks to be infected with at least one type of malware.
The study also found that more than 25% of all devices on a home-office network have one or more services exposed on the internet.
Luckily, the solution is pretty simple.
Encourage your remote employees to use a VPN. I won’t get caught dead without one, especially when using a shared network like my local coffee cafe’s network.
7. Shared Networks
Let me start by saying this: A shared network is any network shared by people. It could be the network at your local coffee place, but it’s most likely also your home network.
While employees may take all the steps to prevent cyberattacks, their family members may not be so careful.
BitSight found that shared networks are at least 7.5x more likely to have five or more different types of malware on them.
Again, the solution is pretty simple.
Encourage using VPNs, regular security updates, and a robust network policy.
8. Webcam Hacking
Everyone’s heard about webcam hacking.
Webcam hacking is when a hacker gains access to a webcam. This lets them spy on users and gather confidential information.
The most common way of hacking a webcam is through malware and security vulnerabilities.
Sometimes hackers also try to get in on your meetings. This is called “Zoombombing.”
Hackers will join a private meeting and often display offensive content or try to steal sensitive information.
The major culprits are shared or stolen meeting links and a lack of meeting control.
So, how do you prevent webcam hacking and Zoombombing?
Easy:
- Use encryption across all of your communications.
- Regularly update your software. Most often, these updates include updates to address security vulnerabilities.
- Use waiting rooms and passwords to protect online meetings.
But my favourite is this: Educate your remote workers. Train them never to share meeting links publicly and to use stronger passwords.
We’ve covered almost nine major remote work security risks and how to mitigate them. Are you ready for the last one? Let’s roll.
9. Vulnerable Chat Platforms
I love messaging apps like Slack. They make collaborating with my coworkers a breeze.
Unfortunately, these apps can also be exploited and cause a severe security risk.
For example, if a chat platform isn't secure, someone could find a way to read my messages without me knowing. They could even pretend to be one of my coworkers to get private information from me.
So, how do you keep your messaging apps safe?
First, only use a messaging app with encryption. In my case, Slack comes with excellent encryption.
Next, do regular maintenance on your messaging apps. Look at the different chatrooms. Are all the members in these rooms supposed to be there?
Also, teach your employees to use secure passwords, two-factor authentication and report any suspicious behaviour.
My Final Thoughts
Now, that was scary and a bit of an eye-opener. I shared 9 remote work security risks and solutions for mitigating them.
At the end of the day, the best security is education. Educate your workers and safely embrace a remote work lifestyle.
